Automatic Server Hardening
Hardening Framework

Created by Christoph Hartmann / Dominik Richter / Patrick Meier
Problem
Physical Security |
Digital Security |
|---|---|
|
?
Out-of-the-box server configurations are insecure and increase the probability of server attacks and data breaches.
|
Solution for Digital Security:
Hardening Framework
In computing, hardening is usually the process
of securing a system:
- Securing default configuration
- Reducing attack surface
- Automatic deployment
- Works on bare-metal and
cloud infrastructures
Honeypot attacks
Measurement of real-world computer attackes
- 6 Million attacks per month
- 200.000 attacks per day
- 8333 attacks per hour
- 138 attacks per minute
Source: Deutsche Telekom Honeypot Infrastructure, August 2014

Information Breached
- Real Names
- Birth Dates
- Government ID Numbers
- Home Address
- Medical Reports
- Phone Numbers
- Financial Information
- Email Adresses
- Username & Password
- Insurance

Source: Bloomberg
Why you should avoid manual server hardening?
Why you should avoid manual server hardening?
- Manual work is not 100% accurate
- Every project needs to reinvent the wheel
- Expensive and time-consuming
- Divergent test & production environments
- No measurement of compliance level
- Requires a lot of resources
Server Scaling
Manual hardening does not fit to autoscaling environments

Server Scaling
Manual hardening does not fit to autoscaling environments

Server Scaling
Manual hardening does not fit to autoscaling environments

Server Scaling
Manual hardening does not fit to autoscaling environments
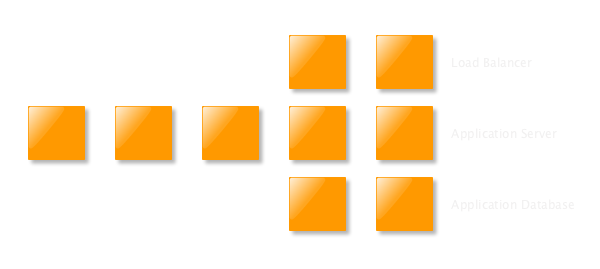
Approach

The Hardening Framework applies secure default configuration while allowing customization for each deployment.
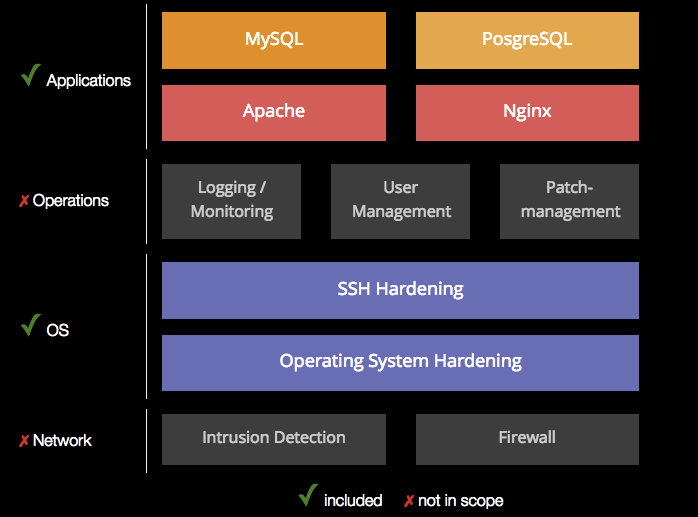
Component Overview

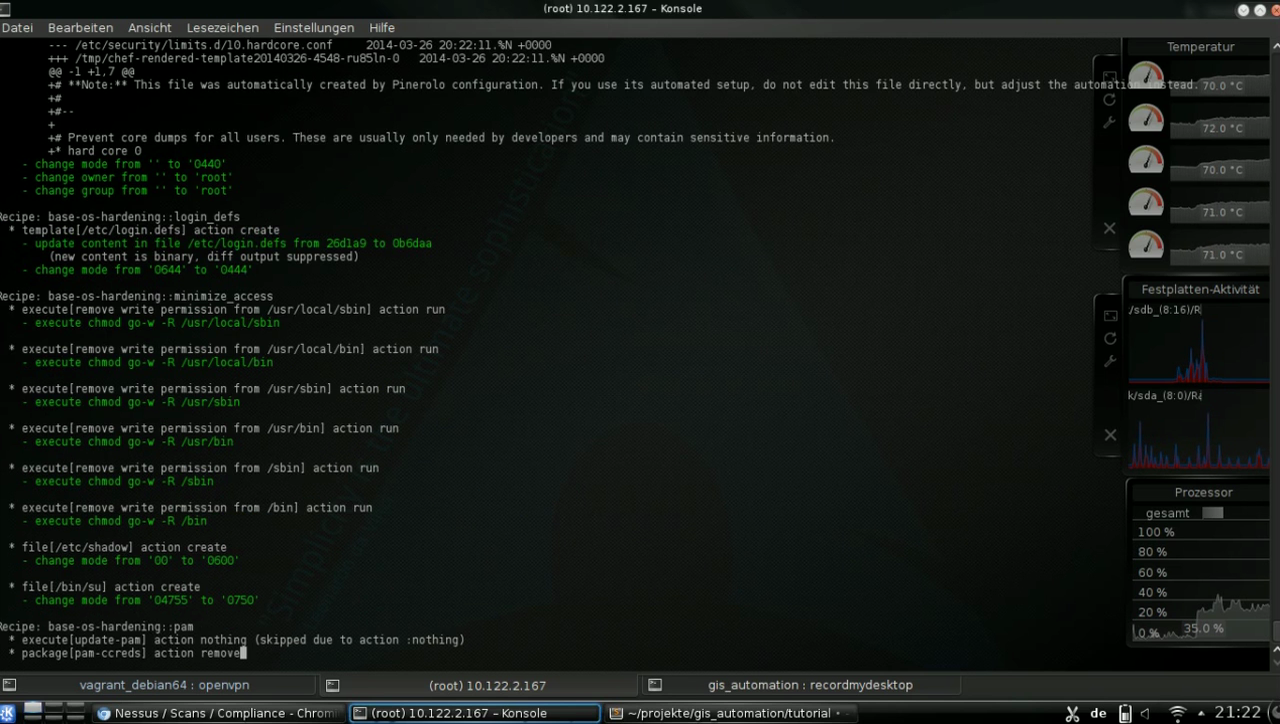
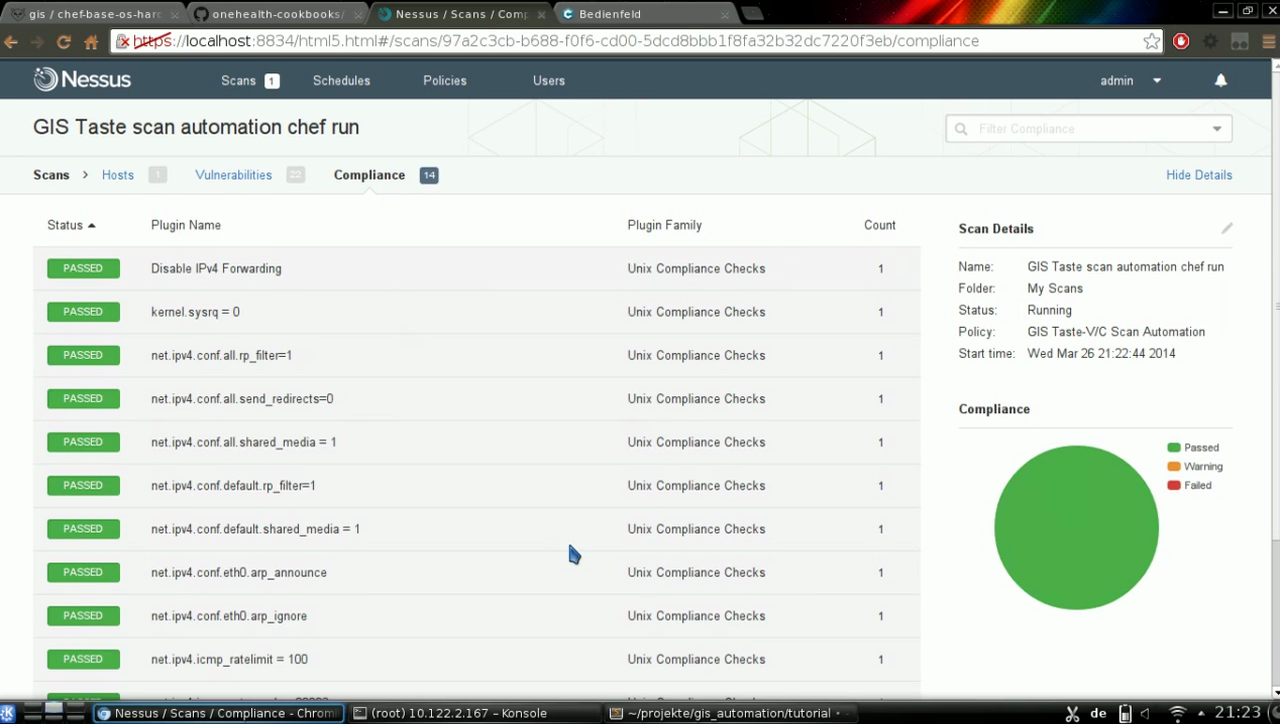
Apply hardening in seconds
| Before | Apply | After |
|---|---|---|
 |
 |
 |
|
|
|
Ingredients
Automation Frameworks |
Infrastructure |
Continous Integration |
Operating Systems |
|---|---|---|---|
|
Core Team
|
Dominik Richter
|

Christoph Hartmann
|
Patrick Meier
|
Edmund Haselwanter
|
Contributors
References
THE END
Further information is available at telekomlabs.github.io




